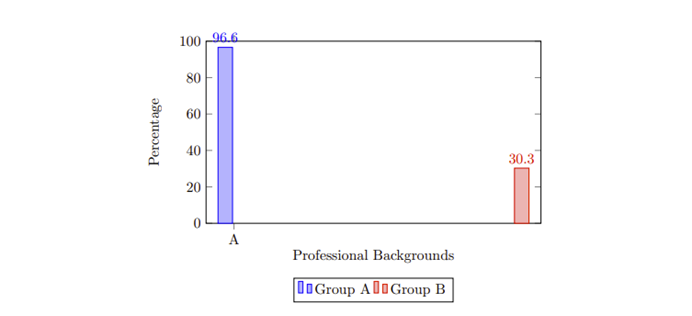
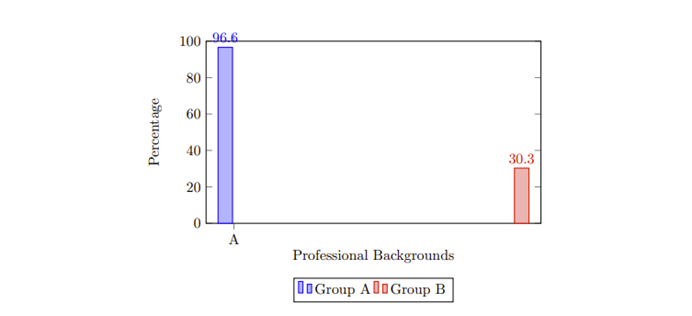
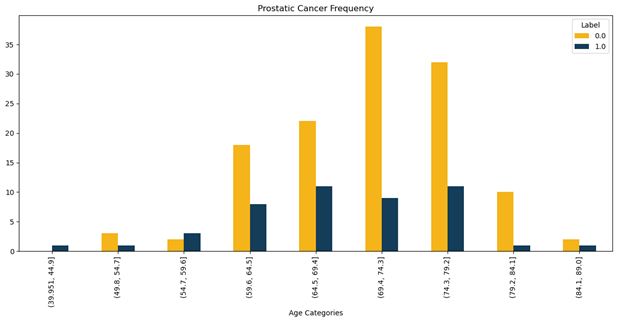
This conference paper discusses the influence of computer vision in self-driving car implementation. The automotive industry has experienced a significant transformation by integrating artificial intelligence, such as computer vision. The global market for AI in automotive has grown remarkably since many organizations in the electric vehicle industry have engaged in computer vision due to its benefits. Object detection in computer vision contributes to autonomous driving systems, assisting self-driving vehicles in classification of the road objects accurately. This paper has provided an overview of the importance of computer vision to self-driving cars, such as user experience, reduction in cost and vehicle safety. However, some challenges, such as adverse weather conditions, have also been experienced. A case study analysis has been done to have practical implications of the self-driving car implementation guided by computer vision for detection.
Research Article
Open Access